While working locally, almost all the fonts we use, come from the %windir%/fonts folder. That is, the fonts are installed into the Windows fonts folder when Windows or any other application is installed. These are trusted fonts and do not pose any threat. When we encounter such fonts on web pages, they are loaded from the local fonts folder. But when the fonts on a webpage are not present on our computer – i.e., the local fonts folder – a copy of that font is loaded into our computer’s memory, and that is when a cybercriminal can gain access to your network.
Dangers of untrusted fonts
When a web page utilizes a font that is already present in the local fonts folder, the browser picks up the fonts from the local folder to render the webpage. Since the fonts in the local font folder are scrutinized by antivirus programs when being installed, they do not pose a threat. When a website or webpage utilizes a font that is not present in the local fonts directory or folder, browsers will need “elevated privileges” to load a copy of the fonts into local memory by downloading them to the computer. Simple downloads are not much of an issue as the antimalware packages will detect if the fonts contain any malware. There is no threat of malware with such fonts. The issue is “elevated privileges” that can be found and exploited by cybercriminals. If they take control of the browser under such a situation, they are capable of doing much harm to not only the computer but to the network as a whole. The best method is to avoid browsers from using “elevated privileges” and that can be done in Windows by blocking the fonts that are not present in the local folder. In such cases, the website will be rendered by substituting the untrusted website fonts with the trusted fonts in a local folder. This may, however, cause the webpage to render improperly and create problems while printing.
Three states available for untrusted fonts in Windows 11/10
There are three options available to you when it comes to untrusted fonts in Windows 11/10. They are: The best method, in my opinion, given the limited number of options, is to block all untrusted fonts and whitelist only those apps that pose less threat via downloading fonts to local memory. Compared to browsers, apps like Microsoft Word, Excel, etc. pose less of a threat as when the fonts are downloaded, your anti-malware is triggered, and if it finds anything objectionable, it will give you a message or block the downloaded fonts. Browsers, on the other hand, are a complex architecture (relying on rendering engines and processors, etc.) so even if the antimalware blocks fonts in memory, cybercriminals may still be able to take control of the machine easily.
Block untrusted fonts in Windows in an Enterprise
Using Registry Editor
To block untrusted fonts in Windows 10 and to whitelist apps that can use untrusted fonts, you will have to use the Windows Registry Editor. As of now, there is no graphical user interface that makes it easier for the admins. The following explains how to block untrusted fonts in Windows 10. Press WinKey+R and in the Run dialog that appears, type regedit and hit Enter key Navigate to: Look for the entry named MitigationOptions. If it is not there, create a QWORD entry of 64 bit and name it MitigationOptions There will already be a value for the QWORD entry we created; copy-paste the following values to BEFORE the value so that the value is there towards the end of the value we pasted.
To turn off untrusted fonts, enter 1000000000000.To run audit mode, enter 3000000000000.To turn it off, enter 2000000000000.
For example, if there is a value of 1000 already in the QWORD we created, it should look like 30000000000001000 Close the registry editor, save work in any other applications that might be open, and reboot the computer. As mentioned earlier, there may be problems viewing the websites or printing when you turn off untrusted fonts. To get around it, it is recommended that you download and install the font manually into the %windir%/fonts folder. That will make it safer to browse the website using that font. Though you can exclude or whitelist apps, it should be done only if you can install the fonts for some reason.
Using Group Policy Editor
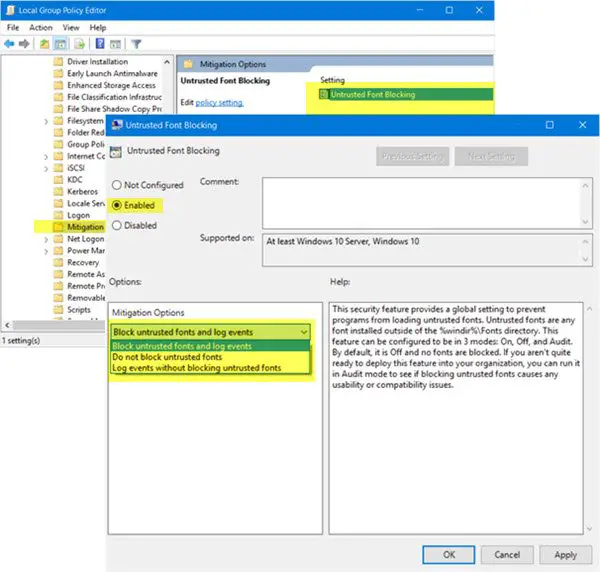
If you use Windows 11/10 Enterprise and Windows 11/10 Pro editions, you can make use of the Local Group Policy Editor. Run gpedit.msc to open the Local Group Policy Editor and navigate to the following setting: Computer Configuration > Administrative Templates > System > Mitigation Options. In the right pane, you will see Untrusted Font Blocking. Select Enabled and then choose Block untrusted fonts and log events from the drop-down menu. NOTE: This policy setting could make your Icons & Web Fonts go missing when you visit a webpage.
How to view log of apps accessing untrusted fonts
If you choose the audit method, you will find that none of the untrusted fonts are blocked. Instead, a log will be created that you can use to see which app accessed which untrusted font type and where, when, etc. details. To view the log, open Windows Event Viewer.
Go to Application and Service Logs/Microsoft/Windows/Win32k/Operational.Under the EventID: 260, you will find all the log entries related to access of untrusted fonts by different browsers and apps during the runtime of the local computer.
An example of the event log would be as follows: This type of entry would be shown when you have completely blocked the untrusted fonts from loading on local computers. It also shows that download of untrusted font happened but was blocked by the policy you created using the Windows Registry Editor. FontType: Memory FontPath: Blocked: true Another example could be: In the above case, the untrusted fonts are not blocked as shown by the entry. It also shows that the browser attempted the download of the fonts to local memory and was used. FontType: Memory FontPath: Blocked: false The above explains untrusted fonts, dangers posed by untrusted fonts and finally, how to block untrusted fonts in Windows 11/10. If you have any doubts or anything to add, please comment. Source: TechNet.